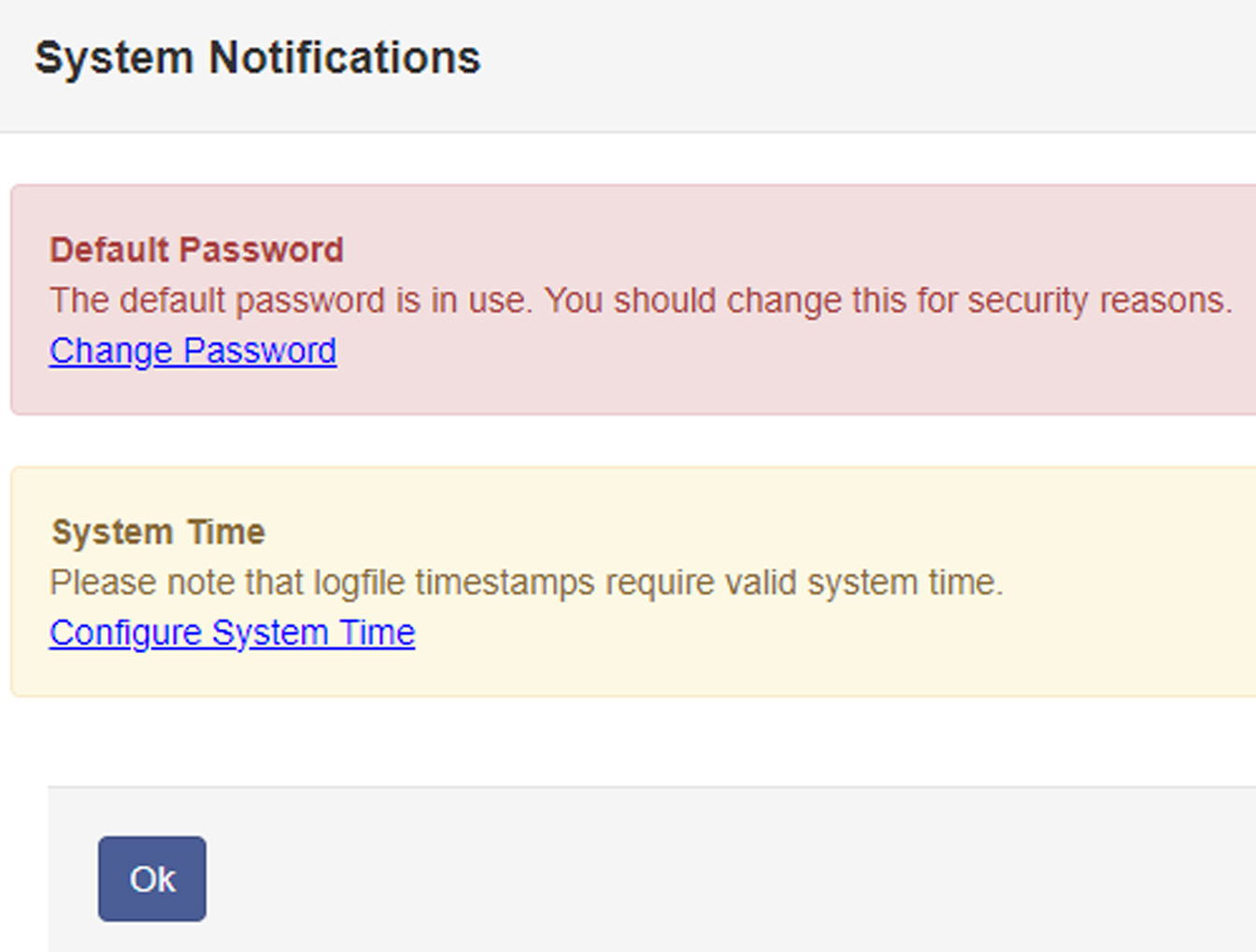
We work hard on the safety of our products. Of course, this also includes commissioning external specialists on our own behalf to independently and critically assess our products and review our safety measures.
Recently we contacted the Electronic Warfare Institute in Canada (EWI) and asked them to perform a complete security audit based on the firmware 2.12 according to UL 2900 Standard (US Cybersecurity Standard). In addition to the UL 2900-1 standard, the Electronic Warfare Institute also focuses on the potential or ability of malware to be be infiltrated into the CS141/BACS. More than 1 million attempts were made within 8 hours with various attack tools with the aim of crashing the web server of the CS141/BACS, or to make the system perform other functions than desired.
They did not succeed! And thus we are one of the few systems that EWI has tested wherein they were unable to find any security vulnerability which can be classified as "High". This goes for all interfaces; especially the operational stability of all hardware interfaces (RS232, RS485) were certified as robust, representing zero points of attack. The final report was surprisingly positive for such penetration tests, but we nonetheless intend to improve.