RCCMD - the World’s most successful Shutdown Software
Cybersecurity Improvements
Cybersecurity Improvements

RCCMD - the World’s most successful Shutdown Software
Cybersecurity ImprovementsRemote Console Command (RCCMD®) is one of the most popular shutdown solutions in the world - hardly any system manages the balancing act between user-friendliness, flexibility, functionality, security and reliability in networks like RCCMD can.
Most shutdown concepts are either :
The lean and resource-saving software architecture of RCCMD runs on almost any operating system, even including ancient operating systems or long discontinued processors like AS400, SUN, etc. What’s more, the handling is remarkably straightforward: for beginners RCCMD provides an intuitive user interface, and for system integrators and experts it acts as a toolbox to manage e.g. virtualized server landscapes with different hardware and software architectures. Also unique is the licensing model, with which individual RCCMD clients can be quickly and unbureaucratically aligned to new tasks; it also allows for seemless sales “further down the pipeline” for our OEM and Reselling Partners. For larger installations with frequent server changes, there is also an RCCMD Corporate license, with which a key may be used up to a defined number of installations.
RCCMD is typically installed within a separate building network, so increased network security has not been an issue until now. However, applications such as RCCMD are now also being used as “gaps” for cyber attacks, so we’ve found ourselves called into pro-action in order to prevent our own RCCMD from being used as such, as well!

The new strategy hackers use isn’t necessarily to attack the usually well-protected servers, but to concentrate more on the server-related assistance systems to circumvent the weaker protection suspected there. RCCMD is designed to work without a constant UPS connection and is therefore difficult to find in the network because there is no constant traffic that can be overheard. However, the knowledge about RCCMD could also have "reached" hackers and GENEREX is aware of the special responsibility towards the users and must now increase the security standard.
1. In addition to the security configuration settings that have been built-in for years -- such as password-authorized channel listing in the network -- the architecture of RCCMD itself serves as the first hurdle that a given attacker will need to overcome. RCCMD is a connectionless client, which means that every RCCMD client installed in the network is constantly listening for incoming messages. This means that 99.99% of the time there is no "message" on the network upon which the attacker can eavesdrop, because such a message is only sent when there is a power outage and the UPS devices start sending messages. The authorization list in the RCCMD configuration is an additional hurdle, since only certain computers are allowed to send a message at all; all other attempts are rejected. These security measures have been sufficient for the last 20 years, but a new sort of threat landscape has arisen and companies are now scanning ALL software products for vulnerabilities, whether they are actually used or not - any outdated libraries will be justly targeted by such security software, regardless of whether they are realistic for use during an attack or not. That's why we "upgraded" RCCMD.
2. With the latest RCCMD version in the GENEREX or OEM download area, we are now introducing a major "security" update. This updates the all software modules and encrypts all communication.
3. RCCMD has always featured password protection, but the default install password was displayed in clear text as a convenience to the user if they couldn't find it in the documentation.
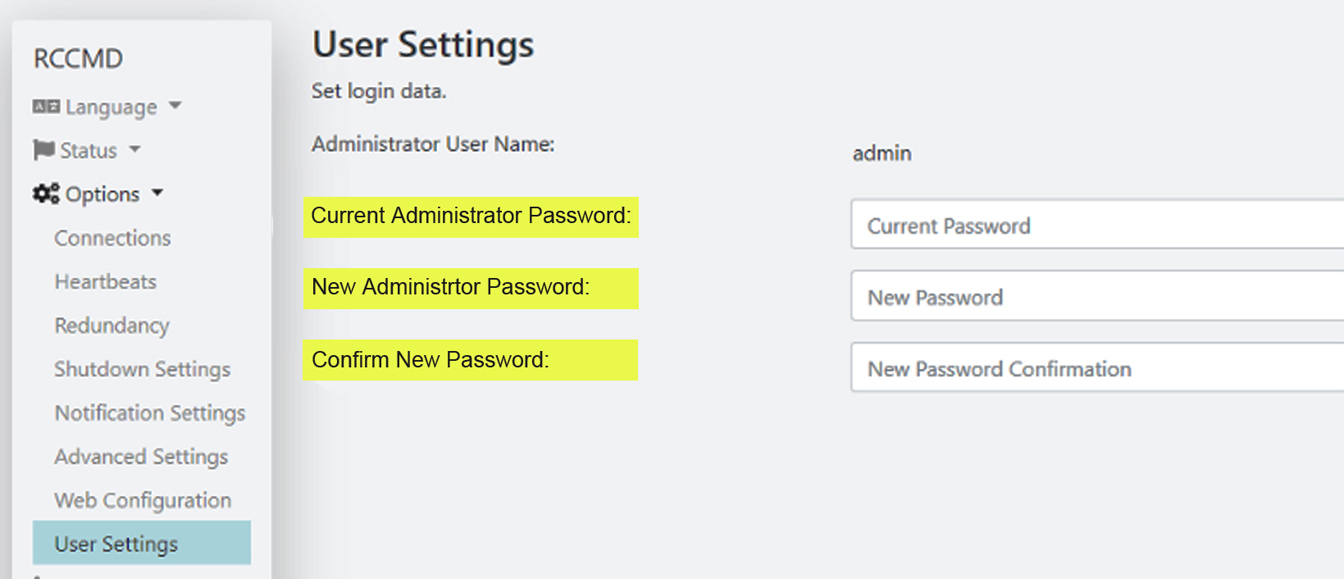
In this way, even inexperienced RCCMD users were able to carry out the initial configuration quickly. This helpful inclusion has now been deactivated; in the future RCCMD will no longer reveal anything about the initial installation password and will also display a message if the user does not replace this initial installation password with one with special cryptic rules.
4. But also on the sender side - i.e. with the CS141, BACS (and all other SNMP cards licensed by GENEREX manufacturers) changes are necessary to protect RCCMD from attacks.
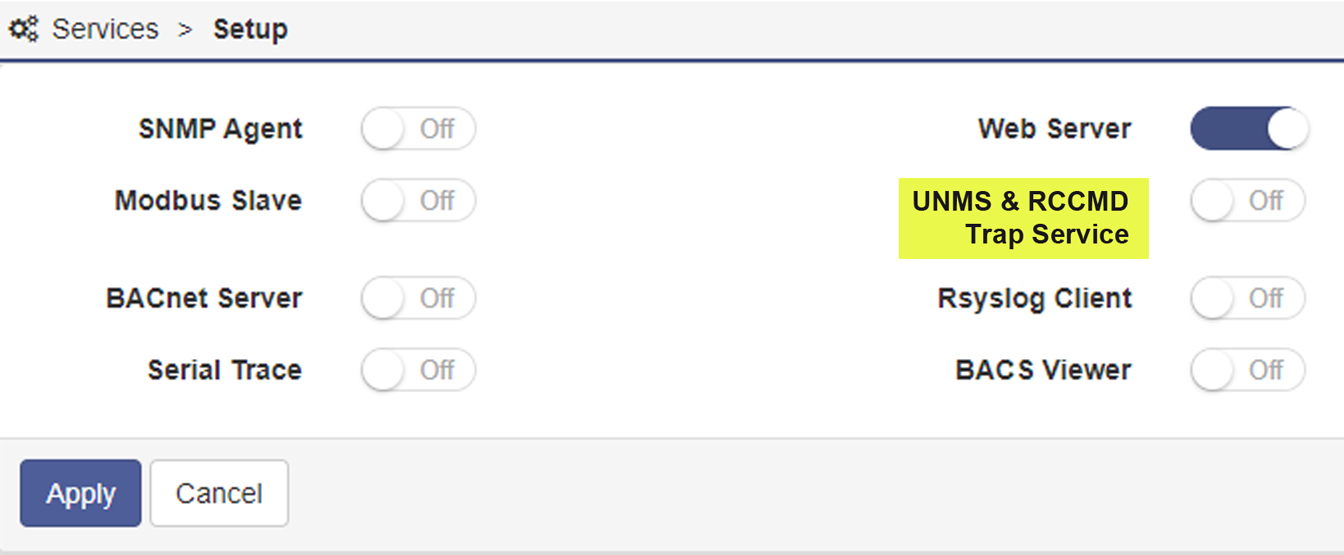
With the CS141 and BACS, e.g. the RCCMD services have been switched off by default upon initial installation. Users who previously simply installed RCCMD clients would then automatically receive a message from the CS141/BACS if there were problems with the power supply. Now, though, a few more mouse clicks have to be made to activate this again: In the CS141 / BACS menu, the "UNMS & RCCMD Trap Service" must now be switched on to restore this functionality.
RCCMD itself is thus largely secure, but of course, we will automatically provide further security updates as soon as new threats become known.
Back to